Not long ago, PCs compromised by malware were put to a limited number
of fraudulent uses, including spam, click fraud and denial-of-service
attacks. These days, computer crooks are extracting and selling a much
broader array of data stolen from hacked systems, including passwords
and associated email credentials tied to a variety of online retailers.
At the forefront of this trend are the botnet creation kits like Citadel, ZeuS and SpyEye,
which make make it simple for miscreants to assemble collections of
compromised machines. By default, most bot malware will extract any
passwords stored in the victim PC’s browser, and will intercept and
record any credentials submitted in Web forms, such as when a user
enters his credit card number, address, etc. at an online retail shop.
Some of the most valuable data extracted from hacked PCs is bank
login information. But non-financial logins also have value,
particularly for shady online shops that collect and resell this
information.
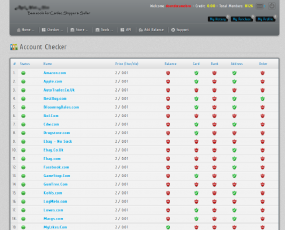
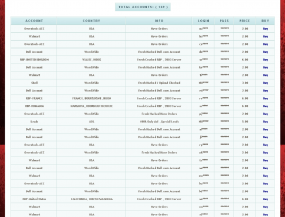
Logins for everything from Amazon.com to Walmart.com
often are resold — either in bulk, or separately by retailer name — on
underground crime forums. A miscreant who operates a Citadel botnet of
respectable size (a few thousand bots, e.g.) can expect to quickly
accumulate huge volumes of “logs,” records of user credentials and
browsing history from victim PCs. Without even looking that hard, I
found several individuals on Underweb forums selling bulk access to
their botnet logs; for example, one Andromeda bot user was selling
access to 6 gigabytes of bot logs for a flat rate of $150.
The “Freshotools” service sells a variety of hacked e-retailer credentials.
Fuente: krebsonsecurity.com
No hay comentarios:
Publicar un comentario