Top 15 Best Security-Centric Linux Distributions of 2019
Being anonymous on the Internet is not particularly the same as surging the web safely, however, they both involve keeping oneself and one’s data private and away from the prying eyes of entities that may otherwise take advantage of system vulnerabilities in order to harm targeted parties.
There is also the risk of surveillance from the NSA and several other top-level organizations and this is why it is good that developers have taken it upon themselves to build privacy-dedicated distros that host an aggregate of tools that enable users to achieve both online autonomy and privacy.
In as much as these privacy-centric Linux distros are targetted at a niche in the Linux community, many of them are robust enough to be used for general-purpose computing and many more can be tweaked to support requirements for virtually any specific user base.
A common factor across almost all privacy-centric Linux distros is their relationship with Tor given that many of them come with Tor’s solid anonymity network service built-in and this, in turn, gives users an environment for them to live in safely without any data logs whatsoever, unlike most VPN providers that will still log your real IP address while still being able to see whatever data you may be transmitting at the point of exit of VPN servers.
However, VPN still has a sheer amount of advantages over the former which makes it somewhat superior in a way (depending on your use case) – particularly, when you put P2P file-sharing, and general Internet speed into consideration, VPN wins here (more on that later).
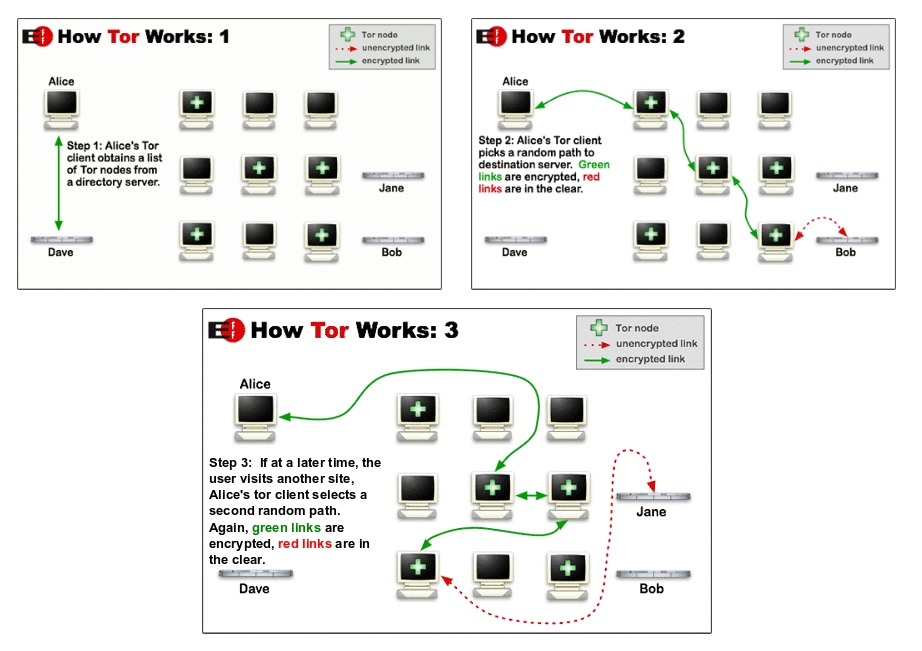
The Tor network secures all network traffic that goes through it by bouncing the data off several random nodes in order to reduce the traffic’s traceability chances. Mind you, during this process, every piece of data is re-encrypted several times as it passes through the randomly selected nodes before finally reaching its destination as illustrated in the images below.
Now that you have a basic understanding of how Tor works to the advantage of its users, here is our list of the 15 Best Security-Centric Linux Distributions of this year.
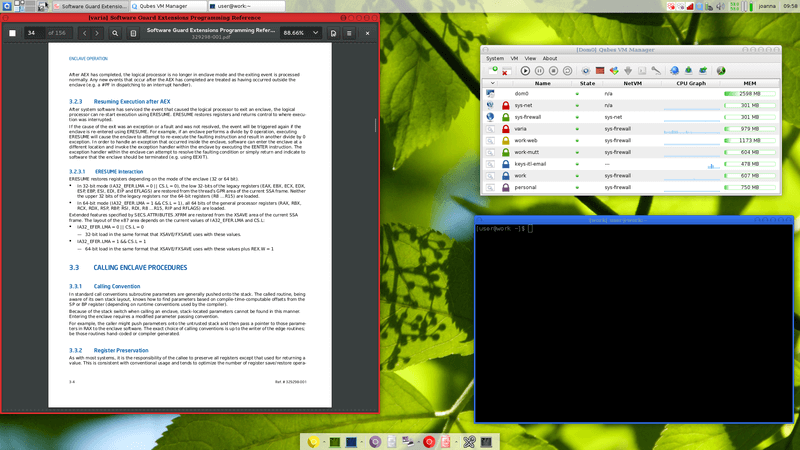
1. Qubes OS
Qubes OS is a security-oriented Fedora-based distro that ensures security by implementing security by compartmentalization. This happens by running every instance of running programs in an isolated virtual environment and then deleting all of its data when the program is closed.
Qubes OS uses the RPM package manager and is capable of working with any desktop environment of choice without requiring a lot of computer resources. Cited by Edward Snowden as the “best OS available today“, it is definitely a good choice if you want to make sure that your identity and data are yours alone whether online or offline.
2. TAILS: The Amnesiac Incognito Live System
Tails is a security-centric Debian-based distro designed to protect users’ identity online and keep them anonymous. Its name stands for The Amnesiac Incognito Live System and it is built to force all incoming and outgoing traffic through the Tor network while blocking all traceable connections.
It uses Gnome as its default desktop environment and being a live DVD/USB, can be conveniently run from a pen drive when it stores all its data in the RAM. It ships with open-source tools that are specially meant for privacy-specific reasons such as MAC address spoofing and windows camouflage, to mention a couple.
3. BlackArch Linux
BlackArch Linux is a lightweight Arch Linux-based distribution targetted at penetration testers, security experts, and security researchers. It offers users all the features that Arch Linux has to offer combined with a ton of cybersecurity tools numbering 2000+ that can be installed either individually or in groups.
Compared to other distros on this listed, BlackArch Linux is a relatively new project yet, it has been able to stand out as a reliable OS in the community of security experts. It ships with the user option to choose any of these desktop environments: Awesome, Blackbox, Fluxbox, or spectrwm, and as expected, it is available as a live DVD image and can be run from the convenience of a pen drive.
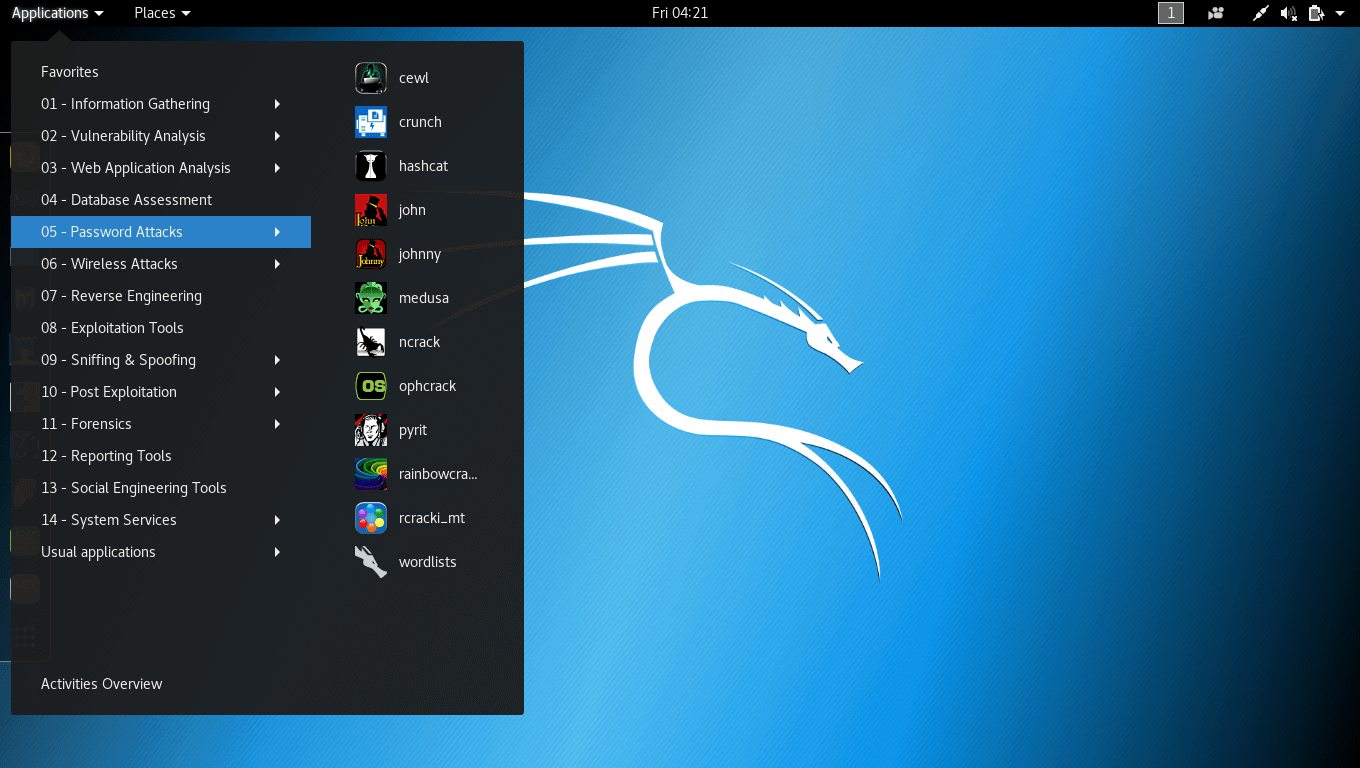
4. Kali Linux
Kali Linux (formerly BackTrack) is a free advanced Debian-based penetration testing Linux distribution designed for security experts, ethical hacking, network security assessments, and digital forensics.
It is built to run smoothly on both 32 and 64-bit architectures and right out of the box it comes with a bundle of penetration testing tools that make it one of the most sort-after distros by security-conscious computer users.
There is a lot more that can be said about Kali Linux (as is the case with every other Operating System in this list) but I will leave the deeper digging for you to do.
5. JonDo/Tor-Secure-Live-DVD
JonDo Live-DVD is more or less a commercial anonymity solution that works in a similar fashion as the Tor given the fact that it also routes its packets via specified “mixed servers” – JonDonym – (nodes in the case of Tor) having them re-encrypted each time.
It’s a viable alternative to TAILS especially if you are looking for something with a less restrictive UI (while still a live system) and a close to average user experience.
The distro is based on Debian and also includes an assortment of privacy tools and other commonly used applications.
JonDo Live-DVD is, however, a premium service (for commercial use) which explains why it is targeted at the commercial space. Like Tails, it doesn’t support any native way of saving files and it goes an extra mind to claim to offer users better computing speed.
6. Whonix
7. Discreete Linux
8. IprediaOS
9. Parrot Security OS
10. Subgraph OS
11. Heads OS
12. Alpine Linux
13. PureOS
14. Linux Kodachi
15. TENS
Fuente: www.tecmint.com
No hay comentarios:
Publicar un comentario